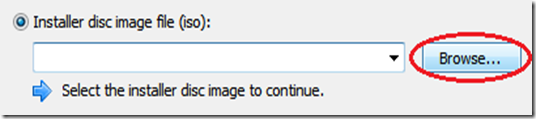
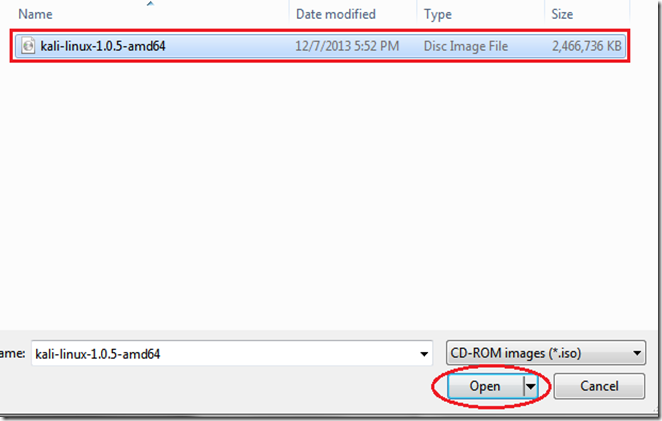
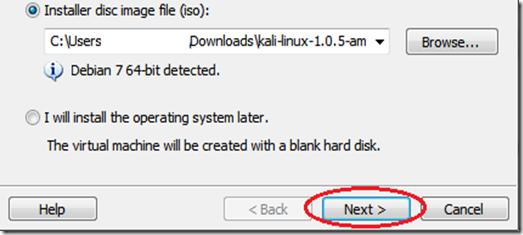
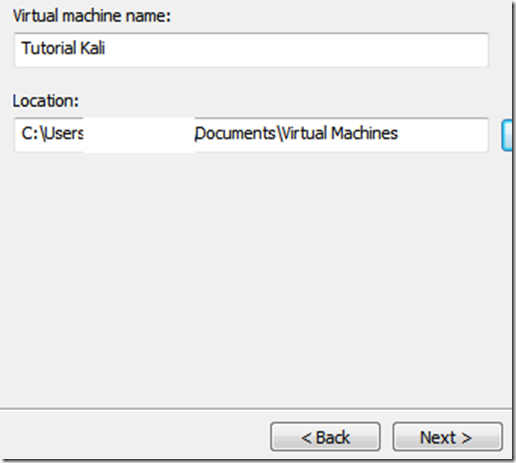
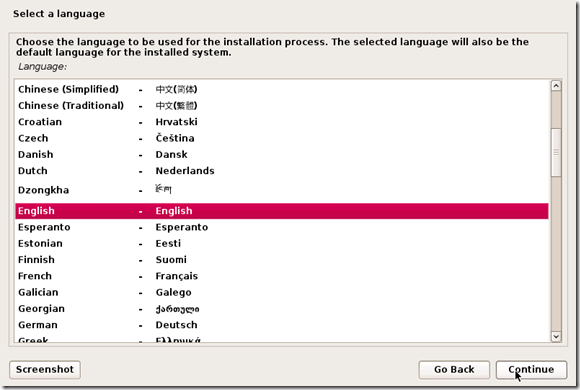
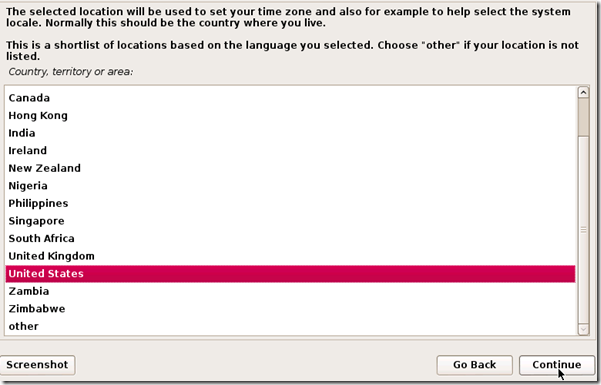
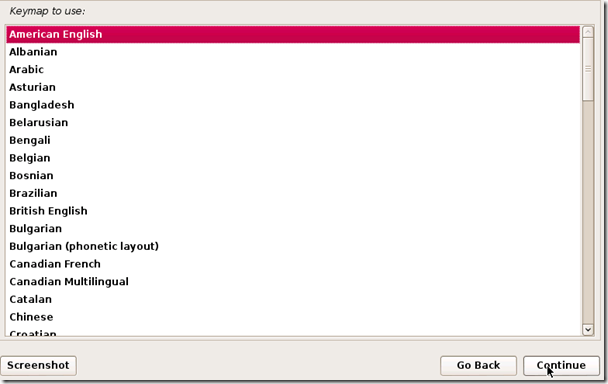
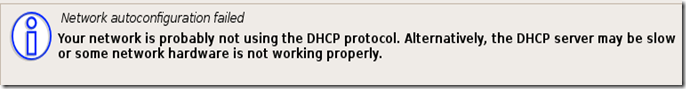
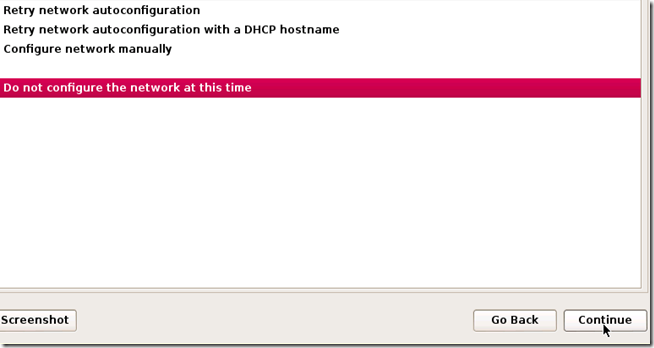
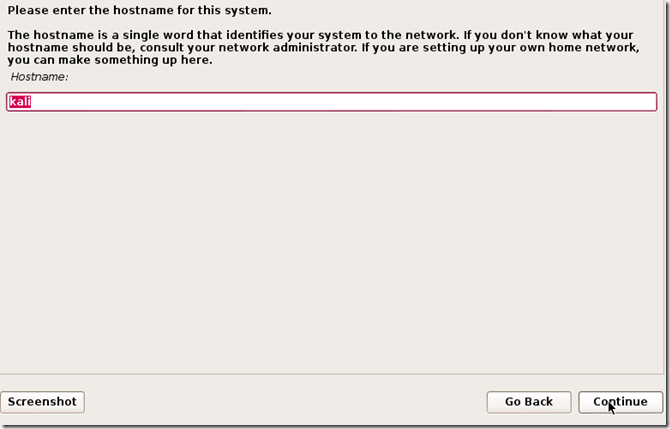
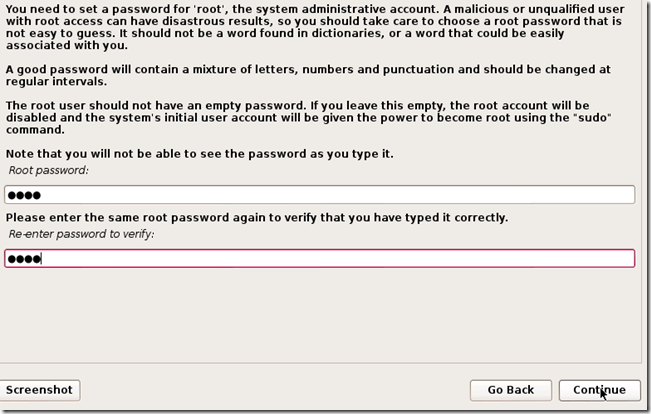
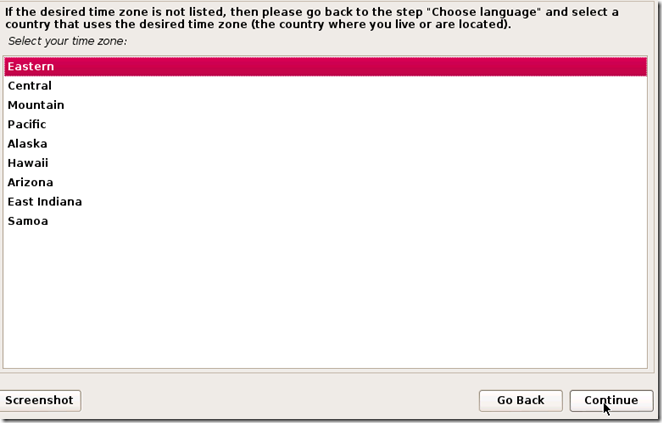
TAKE YOUR TIME AND GET YOUR COMPUTER PROBLEM SOLVED
By Odubanjo Bolarinwa +2348094994773
1. Leaving equipment in plain sight
Someone can easily take your gear if you leave it sitting unattended.
The
typical gadget isn't stolen by thieves who've done lots of planning.
No, most gadget heists are conceived and executed in seconds, and
probably because you left the item unattended. That cozy window corner
at the café is great until you need to run back to the counter for a
refill. A thief can pop in, grab your device, and be gone. Gadgetry is
also commonly snapped up from airport security conveyers (sadly,
sometimes by TSA agents themselves) while you’re waiting for your body
scan. Your locked car isn’t safe, either. An eager crook will happily
smash your window and grab the laptop bag from the passenger seat, even
in broad daylight.
Fix: Don’t leave laptops and other gadgets
unattended. Yes, that means you must either take them to the bathroom or
leave them with someone you trust. At a café, it doesn’t hurt to ask
the staff if you can leave something behind the counter for a minute. In
any case, skip asking, “Can you watch this for me?” and pointing at
your PC across the room.
2. Oblivious gadget usage
Here’s
how street hoods steal your phone. They lurk at the top of the stairs as
you emerge from the subway, or sneak up behind you while you’re
lounging at an outdoor café. Either way, you have no idea they’re there,
because your nose is buried in your smartphone’s Facebook feed. Next
thing you know, you’ve been punched in the face, and the thieves are
dashing off to a getaway car. Can you identify the suspects? No, because
the last thing you saw before it happened was a picture of a puppy.
Fix:
Everyone uses phones everywhere, so it doesn’t feel risky to break one
out on the train or while walking home in the dark. But electronics
remain some of the most easily fenced items on the black market, and it
pays to keep your wits about you when using them in an unknown
situation. Make it a policy to limit mobile device usage to areas where
you’re completely certain you won’t be the victim of a smash-and-grab
attack. That goes double for using your phone while you’re driving.
Don’t become another statistic!
3. Using your devices with dirty hands
Anyone
who has ever handed a cell phone to a child knows that the device will
come back covered in a crust of dirt, crumbs, chocolate, and sneeze
spray.
But you aren’t much better. Playing Bejeweled while
downing a burrito won’t leave your phone looking fresh, and holding your
phone against your face to talk may leave an oily shadow behind.
This
isn’t just gross, but brings health risks, too: The old adage that your
keyboard is dirtier than your toilet applies to your phone, as well.
One report last year claimed that a Ugandan thief contracted Ebola from a
stolen phone.
Fix: Keep an electronics-cleaning vial on your
desk in plain view. Clean your phone, tablet, and other touchscreen
devices daily. Add a quick wipe-down any time you see visible grime.
4. Not cleaning your equipment
We
covered the problem of filthy touchscreens (increasingly problematic in
the Windows 8 era) in the #3 item, above. But what about everything
else?
Literally everything in your high-tech arsenal is
vulnerable to damage from dust and dirt. Grime seeps in through any
crack and crevice, but machines such as desktops, laptops, and even
printers, which have air-intake vents for cooling, are the most
affected. Dust generally won’t damage electronics, but it can clog fans,
optical-drive mechanisms, and other moving parts, which can lead to
component failures and overheating if the fans stop working properly.
Dust in scanners and printers can affect the quality of your printouts,
too.
Fix: Cleaning your equipment isn’t hard, but it’s important
to do so regularly before things build up too much. Once or twice a year
should do it. Can’t remember? Try cleaning out your PC at the same time
you replace the filter on your furnace or air conditioner, or whenever
you get the oil on your car changed. A calendar reminder on your PC can
help, too.
5. Sitting with bad posture at the computer
The
posture lessons, cautionary tales, and ergonomic gadgets of the past 30
years have apparently taught us nothing, and as a result, carpal tunnel
syndrome is the most common form of neurological syndrome called
entrapment neuropathy, affecting 5.8 percent of the population. The
typical treatment, even for moderate cases, is surgery. And all
because you were too lazy to sit up straight.
Fix: Fixing this
problem requires a proper work environment. Keep your chair at a height
so that your knees bend at a 90-degree angle; also keep your feet flat
on the floor, your monitor directly in front with the top of the screen
at eye level, and your keyboard placed so your wrists are parallel with
the floor.
This is easier said than done if, as it is for many,
your office is now a Starbucks. But Imak Computer Gloves can keep your
wrist at the correct typing angle and cushion your hand—an easy solution
that you can drop into your gadget bag.
6. Not taking breaks
Most
parents have no trouble limiting their children’s screen time, but they
find it harder to put down their laptops or smartphones when work
demands action (or Angry Birds chirps).
Breaks are essential to
good health. Your joints, muscular system, circulatory system, and eyes
all benefit from a change of scenery once in a while. Remaining in a
seated position for extended periods of time can cause blood clots
(sometimes even fatal ones). And staring at a screen for hours on end
can cause eyestrain that may affect your vision afterward and make it
dangerous to drive home.
Fix: Fortunately, programs such as
Scirocco Take a Break, mobile apps, and Web browser plug-ins can remind
you to step away from your gadgets, stretch your legs, get a drink of
water, or call it a day on your computer time.
Another easy way
to remedy the problem is to keep, at all times, a very large glass of
water at your desk (the solution for another bad habit: failure to
hydrate). Sipping a gulp from that glass of water regularly will force
you to take an occasional break to the bathroom.
7. Working with your laptop on your lap
Worst Tech Habit
Photograph by Robert CardinA laptop on your lap can mean bad posture and problems from its heat.
Yes,
they call it a laptop, but you weren’t supposed to take that literally.
Using your laptop on your lap can lead to a whole host of problems,
many caused by the heat that most laptops spew from their undersides.
The maladies can range from simple skin dryness and discoloration to
reduced sperm count to—the jury’s still out on this one—cancer.
Heat
isn’t the only problem. Placing a heavy object across your thighs for
hours on end can cause neurological damage, particularly when coupled
with the typical laptop-on-lap posture: hunched over, legs outstretched,
neck craned. Arthritis can also develop over time.
Fix: Fixes
aren’t easy unless you want to move your desk into the living room so
you can watch Game of Thrones while you work. Instead, start with a lap
desk that shields your thighs from heat, and follow the break-taking
tips outlined in item #6. Periodically shifting your laptop from one leg
to the other can help. Avoid working on your laptop with your legs
outstretched on the coffee table, too. Your nervous and muscular systems
will be in better alignment if you keep your knees bent and your feet
on the floor.
8. Failing to back up data
Stop me if you’ve
heard this one before. Everything is zipping along just swimmingly
until one day it suddenly isn’t. Maybe it’s a hard-drive crash, maybe
it’s a malware infestation, maybe it’s a stolen laptop. One way or
another, your data has abruptly vanished, and you’re left crying that
you should have been backing up your data.
The excuses for not
backing up your data are becoming increasingly thin. Any number of
online backup services will sync your files automatically with a
cloud-storage system, whether you use a PC, a tablet, or a phone. Don’t
be lulled into thinking that you have nothing important on that device.
Whether it’s a forgotten baby picture or a game save on the verge of
hitting 100 percent completion, you’ll feel differently once it’s gone.
Fix:
With most backup systems now, you don’t need to do anything except
install an app and set it up. If that’s too much effort, well, perhaps
it’s time to go back to pen and paper.
9. Reusing passwords over and over
We are all guilty when it
comes to this bad habit. How are you supposed to remember your 100th
different password for the latest social network you’ve joined? You take
the easy way out and reuse a password that has worked for you time and
time again.
Password “strength” is a bit illusory. All it takes
is one website that doesn’t store passwords securely and gets hacked, or
one old and unencrypted hard drive that’s sloppily disposed of, to
bring the whole house of cards tumbling down, no matter how many
numbers, uppercase letters, and special characters you use.
Fix:
The solution involves coming up with a system to build a unique password
based on each website where you use it. Build from a base phrase and,
for each site, add something unique to it. Take, say, Flurpb&rgl3r
as a base and add fb8 to the end for Facebook, or tw7 for Twitter. (In
this example, the numerical component of the end tag is the number of
characters that the site name has.)
Presto: a password that you won’t forget but is virtually impossible to crack.
10. One account, multiple users
A
parent’s typical move, when giving a child his or her first computer,
is to hand it over and hope for the best. Mom then wonders where her
address book went, and her boss wonders why she sent him 20 email
messages full of gibberish.
Fix: Setting up multiple user
accounts on Windows isn’t difficult, and it’s an incredibly prudent
precaution if more than one person is going to use the machine. Never
mind the privacy issues—accidents happen, even among grown-ups sharing a
PC. Having two people working on different files called “resume.doc”
can only end in heartache.
For children, security and safety are
bigger concerns. Setting up kids with Standard User accounts (instead of
Administrator) is the wise thing to do to keep unwanted software from
being installed, and it’s the key to letting you configure parental
controls on the computer, as well. So next time Junior wants to use your
PC “real quick, just to look something up,” tell him sure, and give him
his own account.
11. Failing to update
Software published
today is updated on a near-constant schedule. If you have a few dozen
apps on your smartphone or tablet, you’ve probably become accustomed to
downloading updates on a daily basis—unless you’re one of those people
who never update anything.
Software updates are released for a
variety of reasons. The application’s developers add features, fix bugs,
and plug security holes. Installing updates upon release—particularly
operating system updates and security software updates—is essential to
keeping your device stable and secure.
Fix: Every application has
to be updated, so it’s forgivable if you don’t want to deal with the
constant nagging to install, reboot, and repeat every day. Automatic
updates take some of the hassle out of this operation, but most software
updates today still have to be manually installed. There’s no easy
solution to this. If immediately installing updates when they appear in
the system tray or on your handset doesn’t fit with your computing
habits, make it a weekly event to update everything all at once—perhaps
after you take out the trash.
12. Printing anything
Worst Tech HabitsPhotograph by Robert CardinSave paper and don’t print anything. Your documents are (or can be) archived online.
You’ve
seen the request at the bottom of so many email messages: “Please
consider the environment before printing this email.” Is that really
necessary in 2013? Who is not considering the environment? And more
important, who is still printing out their email?
In an age of
$75 terabyte hard drives and endless cloud storage, why does anything
that starts out in digital format, such as email, ever need to go back
to paper? Even utility and bank statements are archived online (often
for years), much safer as backups than the ones sitting in file cabinets
in your house.
What legitimately needs to be printed? The only
thing I can come up with is mailing labels for products that have to be
physically shipped somewhere, and maybe the packing slips or receipts
that are included with those packages. Also arguably acceptable is the
occasional printed photograph that you’d like to frame and put on the
wall.
Fix: Unplug your printer and stick it in a closet for a week. See if you can’t go paperless, cold turkey.
13. Faxing, ever
As
bad a habit as printing is, faxing is infinitely worse. Here, you have
the opportunity to break the paper cycle, but instead you’re continuing
it, indeed worsening it by duplicating the paper and possibly racking up
long-distance telephone charges in the process.
No disrespect to
the fax machine. It was a critical piece of apparatus in American
business for years, but now it is an outdated relic on a par with the
dial-up modem. Yes, technology has improved—you can even send color
faxes now—but quality really has not. Most faxed documents are still
difficult to read, still come out askew, and are often incomplete, cut
off by a paper jam or a problem with the phone line. Many people resort
to faxes when they need to send a signed document to another party, but
in many cases a fax with a signature may not even be legally acceptable.
Fix:
Fortunately, for most people, faxing is a fairly easy habit to break.
Just staring at the pile of junk faxes that most businesses continue to
receive is impetus enough. While your fax machine may be attached to an
otherwise useful all-in-one printer, you can simply unplug it from the
phone line, and save a few bucks a month if you’re paying for a second
line for it. Plenty of free or cheap services can let you send a digital
fax, should you really need to do so.
14. Throwing computer equipment in the trash
If
you’ve been a computer user for any length of time, you’ve probably
accumulated dozens of old peripherals, outdated or broken laptops,
ancient cell phones, and gobs of cables. What do you do with that
mountain of telephone wire that came with every modem you ever bought?
What about all those old red-white-and-yellow A/V cables bundled with
the VCRs of yesteryear?
Much of this material unfortunately ends
up in landfills. Some, like telephone wire, isn’t exactly hazardous, but
anything with a battery or a circuit board in it probably is. (Modern
electronics typically aren’t as toxic as older stuff, but that isn’t
what you’re throwing away, is it?)
Fix: The good news is that you
can fairly easily recycle most of this junk, even broken cables and
defunct printers. E-waste events are common in many neighborhoods, and
both Goodwill and Best Buy will take just about anything off your hands
for reuse, resale, or recycling.
Don’t forget to scrub personal
data from any hard drive or flash drive you recycle. Use a multipass
wiping tool such as BCWipe to make sure that last year’s tax returns
don’t end up in someone else’s hands.
15. Not reading the FAQs
When
trouble arises online—as it always does—the knee-jerk reaction is to
open a support ticket or call the help desk immediately. Then you’ll
spend half an hour on hold waiting for someone who probably can’t do
much to help you.
Fix: Make it a habit to remember the FAQs.
Companies love to create Frequently Asked Questions pages because they
really do answer a lot of common concerns. While some FAQs are more
thorough than others, they’re always worth a quick spin to see if you
can’t find a quick answer to what you believe is a unique problem. Use
the search feature on your browser to scan a large document for your
trouble keywords.
16. Oversharing on social media
It’s
good news that you finally resolved your bunion problems. We got a kick
out of that picture of the syrup puddle on your breakfast waffles. And
the story about the squeaky dog toy you bought was also a gem.
Yes,
complaining about banal stories, photos, and comments on Facebook and
other social media sites has become a First World Problem of the
greatest order, but considering how intertwined social media and the
business world have become, the person likely to suffer the most is the
one who does the blathering.
Fix: If you’re at all concerned
about your appearance in the world, try to keep comments unique and
unexpected. Dutifully copying the latest “Follow these instructions or
else!” post on Facebook is no better than mailing chain letters to all
your friends. Restrict social media chatter to a few posts a day. You
can post the rest of your conspiracy theories ad nauseam to your blog.
17. Texting at the table
Worst Tech HabitsPhotograph by Robert CardinTexting at the table when someone is talking to you should be a no-no.
Really?
It’s that important? We all love our smartphones, but using them in the
company of others, particularly at mealtime, is just plain rude. (It’s
also gross. See item #3.)
What about the phone-in-the-lap trick?
Not kosher. Even Emily Post says so. And that goes for any kind of
social situation, whether it’s school, work, or a simple conversation
with someone else.
Fix: If you must deal with another
conversation, voice- or text-based, take it to another room or outside.
And be sure to make the “no phones at the table” rule apply to everyone
in your household, including yourself
18. Using your phone or tablet without a case
How
will it end? Eventually your phone or tablet will die. The battery may
explode. The CPU may melt down. Cosmic rays may fry the RAM. But
realistically, you will probably just drop it.
No matter how
sure-handed you are, and no matter how carefully you treat your devices,
one day they are going to slip out of a pocket, or simply fall to the
ground when someone’s elbow bumps against you.
Fix: The only
solution is to enshroud your gadgets in cases—thick, sturdy ones. The
flippy Smart Cover for your iPad is useless when a preteen fumbles it to
the tile. Go for a thick rubber or silicone case that covers every
corner of the device, such as the Otterbox Defender. A thinner, plastic
case may do the job, but replace it when it becomes damaged.
19. Failing to pick up the phone
Worst Tech HabitsPhotographs by Robert CardinA blanket policy of ignoring your incoming calls may not make sense.
The
phone rings. You look at the number and don’t recognize it. You let it
go to voicemail, and that little red light blinks all day until you
finally get around to playing the message.
Technology has given
us a half-dozen ways to communicate with one another—virtually all at
the expense of the fastest and most expedient, the telephone. It’s
easy to understand why we don’t answer the phone anymore: We likely
don’t want to talk to a solicitor, a pitchman, or a robotic
telemarketer.
Fix: We’re not talking about breaking the rule
against texting at the table (item #17), but a blanket policy against
answering the phone may not make sense. Consider how much faster it
would be to answer a simple question via voice than to read and respond
to a long email message. Imagine that your $500-an-hour attorney is the
one who is calling. Do you really want to force him to spend 10 minutes
writing an email to you when he could have told you something on the
phone in 30 seconds?
20. Failing to silence your phone
These
days, just about every public performance begins with an entreaty to
the audience to mute or turn off their cell phones. Thirty minutes
later, the unmistakable jingle “Marimba” makes its presence, and its
clueless owner, known.
Cell phones that erupt at the most
inappropriate times are a cultural epidemic, and ironically it’s likely
because we have heard so many commands to shut our phones off that we
simply don’t hear them at all anymore.
Fix: While you likely
can’t fix the behavior of the person sitting next to you, at least you
can ensure you aren’t part of the problem. Simply make your default
setting “ringer off.” Turn the ringer on only when you know you’re going
to need to hear it ring—that is, any time it’s not in a pocket and out
of arm’s reach.
21. Never rebooting
For all their advances
in reliability, our gadgets remain incredibly susceptible to minor bugs
of all kinds. Memory leaks are still rampant in Windows applications,
flooding your RAM to make it unusable. Numerous applications still
require reboots after they’re installed or updated, and the app will be
stuck in limbo until that reboot occurs.
Windows 8 has improved
reboot times (and reboot frequency), but every operating system—whether
desktop or mobile—benefits from an occasional reboot. Think of it as a
good night’s sleep for a device: A reboot lets it start fresh, free of
digital baggage. A reboot may improve your device’s battery life.
Fix:
Build rebooting into the natural downtime of your day, typically when
you go to bed. Reboot your device to give it a refresh. Better yet, turn
it off completely and save energy.